It’s hopefully well known by now that Bluetooth’s baby brother, BLE, isn’t exactly stellar when it comes to security. What you save in battery life and complexity comes at the price of easy discoverability and exploitability. Whilst BLE does have support for security, it is rarely implemented. When it is implemented it’s often done poorly.
BLE isn’t difficult to attack.We gave a short demo and explanation at BSides Manchester this year. There are some good guides and tools out there, but the consequence of compromise isn’t often particularly significant. However, one category of smart device we found that often had weak BLE security were smart sex toys. You’ll doubtless know that we were shocked how easy it was to hijack a wi-fi camera dildo, we updated this work at SteelCon and reviewed a number of smart adult toys that used Bluetooth.
The other big issue is the lack of RF range, meaning that it isn’t easy to find devices in the absence of a http://wigle.net equivalent for Bluetooth. So we went hunting… and found some devices in an exploitable state… in people.
We had to give this a name. It didn’t take long: hunting for Bluetooth adult toys = screwdriving.
Shortly after I started at PTP, I took interest in a colleagues project reverse engineering the camera vibrator. Rather loudly, I announced in the office that I had a smart butt plug…. for research.
So of course my colleagues suggested that my next project should be to reverse engineer it.
And here it is, the Lovense Hush:

Adult toys lend themselves to being great testbeds for IoT research: they’re BLE, they’re relatively cheap, they’re accessible and have companion apps for the full spectrum of testing.
So let’s look at the Hush a bit more
Using your favourite BLE sniffing hardware (we used a Bluefruit but an Ubertooth is just as great) you can visualise the BLE packets in Wireshark.
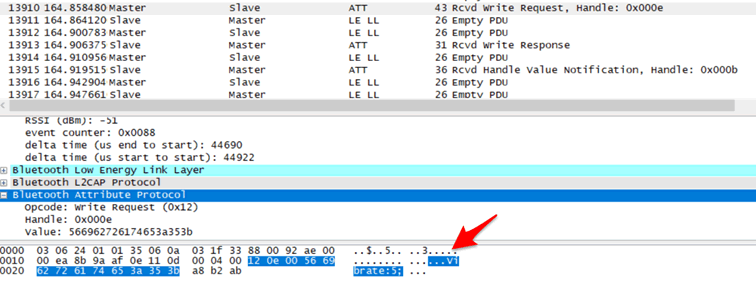
In this case we can see the app has caused the Hush to start vibrating when the handle 0x000e has “Vibrate:5” written to it:
We can also start to replay commands from within Kali, so no smartphone app is required.
Bring up your Bluetooth dongle (a cheap £5 job will do if your laptop doesn’t have one):
# hciconfig up
Scan for BLE devices to get their MACs:
# hciconfig lescan
Start gattool in interactive mode:
# gattool -I > connect <MAC of the Hush> > primary > char-write-cmd <characteristics> <hex>
That output of primary should give you the same handles that we saw flying over the air earlier.
<characteristics> is the handle from above (0x000e) and the <hex> string is the value of Vibrate,10 (or whatever strength you like): 766962726174652C3130
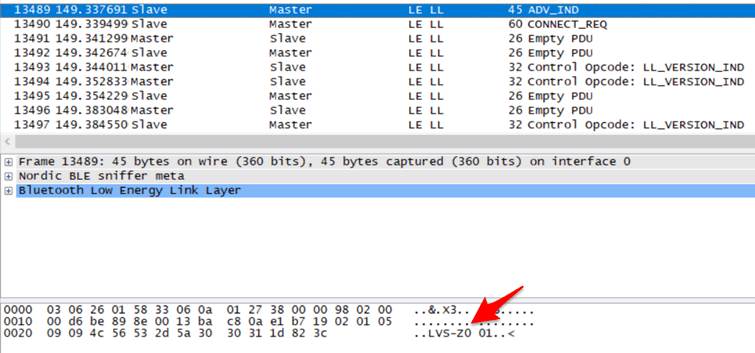
BLE devices also advertise themselves for discovery, which anyone can find, in this case the Hush calls itself LVS-Z001 – this is the same across all Hush devices we’ve looked at, so it’s like a unique fingerprint.
Note that there is no PIN or password protection, or the PIN is static and generic (0000 / 1234 etc) on these devices. This isn’t a problem just with the Hush, we’ve found the same problem in the following:
- Kiiroo Fleshlight
- Lelo
- Lovense Nora and Max
In fact, we’ve found this issue in every Bluetooth adult toy we’ve looked at!
The challenge is the lack of a UI to enter a classic Bluetooth pairing PIN. Where do you put a UI on a butt plug, after all?
The only protection you have is that BLE devices will generally only pair with one device at a time, but range is limited and if the user walks out of range of their smartphone or the phone battery dies, the adult toy will become available for others to connect to without any authentication.
But surely you’re not going to find these things outside people’s houses?

Finding Bluetooth adult toys
Recently I was in Berlin, walking with a Bluetooth discovery app, this one is Lightblue. I was genuinely surprised to see the Hush BLE name, LVS-Z001, pop up:
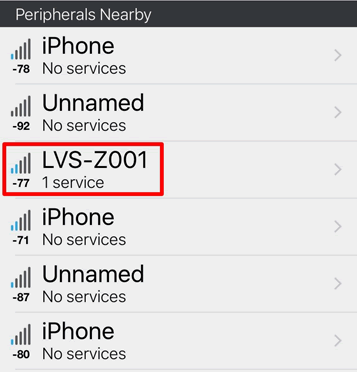
BINGO! This is genuinely the discovery of a Hush plug, ready and waiting for anyone to connect to it, on a public street.
I wonder when we might see a http://wigle.net but for BLE and ZigBee? The wigle Android client already supports Bluetooth stumbling, though the site doesn’t maintain a catalogue of Bluetooth networks. It clearly wouldn’t take much.
I should say at this point that this is purely passive reconnaissance based on the BLE advertisements the device sends out – attempting to connect to the device and actually control it without consent is not something I or you should do.
But now one could drive the Hush’s motor to full speed, and as long as the attacker remains connected over BLE and not the victim, there is no way they can stop the vibrations.
It’s important at this point to say that we’ve not set out to kink-shame anyone for their use of these devices: adult toys appeal to a huge spectrum of people and their ubiquity allows people to enjoy a sex-positive life, however we think that these same people should be able to use them without fear of compromise or injury. Talking about these issues will hopefully lead the industry to improve the security of its toys.
Having an adult toy unexpectedly start vibrating could cause a great deal of embarrassment.
Hearing aids
Here’s another example of body-worn BLE equipment open to anyone:
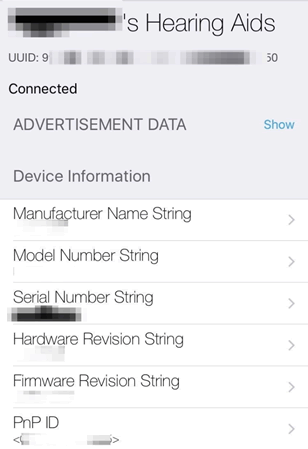
These are my Dad’s hearing aids, I managed to find them broadcasting whilst we were having lunch one day. They have BLE in them to allow you to play back music, but also control and adjust their settings (like if you’re in a noisy restaurant or a concert hall). These things cost £3500 and need to be programmed by an audiologist so not only could an attacker damage or deprive someone of their hearing, but it’s going to cost them to get it fixed.
Fixing this
There are several ways for this issue to be resolved, here are some of them:
Physical interaction
These devices will be connectable when not currently connected to another Bluetooth device. This should not be the case. Physical interaction such as a button push should be required for it to enter a state which allows connections.
Signal strength
When in a state that allows connections, the Bluetooth signal strength could be dropped to a very low value, meaning that the device it’s connecting to needs to be physically adjacent in order to pair. Yes, with a high gain antenna one could probably fool this, but it reduces the risk significantly.
Unique PIN per device
Loading a configuration at the factory could allow for a unique PIN to be created for each adult toy. This is an expensive option, as devices will have to be powered up and flashed. A PIN sticker per device will also add cost.
Numeric comparison
Other options include numeric comparison, though I accept that putting a keypad on a butt plug is a bit of a non-starter!
Issues that can’t be fixed
BLE advertises its presence. As a result, these toys can be located fairly accurately using triangulation. How comfortable do you feel knowing that if you wore such devices in public, that you might be discovered? Not a concern to some, but very concerning to many.
One solution would be a generic BLE device name, so the adult toy couldn’t be distinguished from say a Bluetooth printer? Still potential issues with MAC addresses, but much harder to tie down to a specific device.
Several researchers have created maps of small city areas using drones, mapping various RF protocols. How long before someone flies a BLE mapping drone? There’s already a drone-based Zigbee device map of parts of Austin, TX.
The specification for Bluetooth 4.0 allows for only one concurrent master and slave connection at once. That offers a layer of protection, as if your phone is connected to your adult toy, it’s difficult to either de-auth or jam the connection and connect a rogue device. Not necessarily impossible to do so though.
However, Bluetooth 4.2 changes this:

This opens up the opportunity for a rogue master device to be connected concurrently to the legitimate master. This could allow for any BLE device that does not enforce pairing or bonding to be simply connected to by a rogue.
Next steps
The next part of this project is to fully reverse engineer the butt plug and pull its firmware. Some careful work with a scalpel will be necessary, but I’ve already got hold of the PCB images from the FCC web site.
Here’s the inside of a smart butt plug.
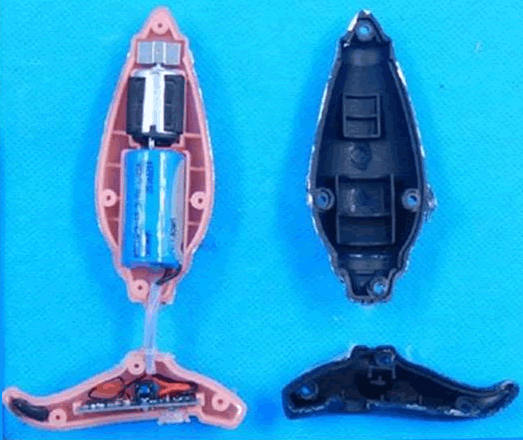

To conclude, the next time a client, or anyone else for that matter, tells you that eavesdropping or controlling BLE devices is a purely hypothetical attack, point them at this post.
If this post has piqued your interest in teledildonics then we recommend you follow @internetofdongs.