Silent Circle do some quite cool call encryption software.
Between the Silent Suite and the Blackphone, I really like what they’re doing and greatly respect their key players.
However, their recent marketing piece annoyed me, because the key message about cracking short PINs was both correct, wrong and misleading all at the same time.
Here’s the image they promoted:

The key message about short PINs is a good one
4-digit PINs aren’t really enough. Remember that the PIN is usually also the encryption key for the data on the device, so potentially every set of cached credentials, every password to every app you use, is protected by 4 numbers…
But the point about cracking a 4-digit PIN in 1.25 minutes is totally misleading
The story is actually about cracking the encryption key for the phone, not the phone PIN. Whilst they’re usually the same thing, the crack time quoted is actually from when working on an IMAGE captured from a phone.
Capturing that image is a whole different matter. The potential for extracting an image depends on many different factors; phone O/S, hardware, firmware and software version etc.
For example, in the case of Android, the PIN is usually also the encryption key or KEK. The article correctly discusses the different hashing methods for the various Android versions and also the speed of the crack.
However, it doesn’t discuss the challenge of capturing the image first. For example, depending on the phone manufacturer, it may be possible to capture an image from the JTAG ports. This is usually more successful for Android, compared to iOS.
Real world cracking times
Most phones have a lock out after a number of PIN attempts. That dramatically increases the time required to break in to a phone.
Devices such as the IP-BOX can break in to an iPhone using brute force. A 4-digit PIN takes up to 17 hours to crack in this way. Yet, as far as I know it doesn’t work on the latest versions of iOS (8.1.1 / 8.1.2 as far as I recall).
Then, if you’ve enabled the Android Debug Bridge (part of the developer options) then you open your ‘droid handset to a PIN crack in about 16 hours for a 4-digit PIN. But few users have enabled ADB on their handsets.
In none of the above cases is a crack in 1.25 minutes likely!
So, the message that Silent Circle were promoting should really be:

What should you do?
Hopefully your corporate MDM makes it easy for you to enforce a 6-digit PIN as a minimum. If not, it’s easy to set a long PIN.
iOS is a little counter-intuitive
First, disable simple PIN:
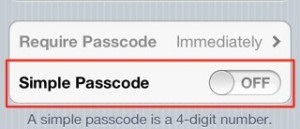
The next step often scares users off a bit, the whole keyboard is presented:

“I don’t want to put in letters too” they say. However, if you only choose numbers, only the number pad pops up when unlocking the phone.
Android is much simpler
Several options are offered and it’s quite obvious how to set a long PIN.
Avoid face and voice unlock though. These have been shown to have security issues.
Touch unlock / TouchID
I’m undecided about using biometrics such as fingerprints to unlock a device. Granted, they make shoulder surfing and related attacks much harder
However, bear in mind that your biometric is potentially stored on the phone. If the fallback PIN is cracked, you may now have a compromised fingerprint.
If you have a password compromised, you throw it away and create a new one. If your fingerprint is compromised, what then?














