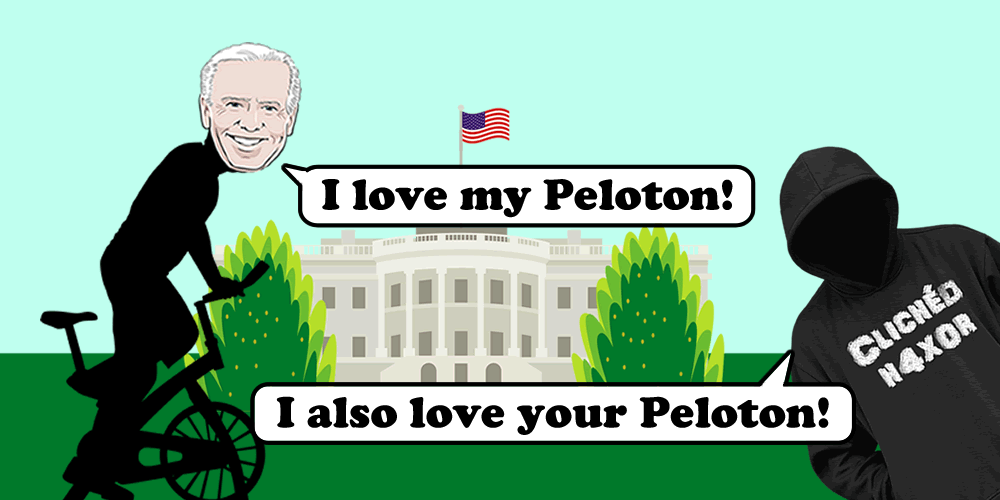
An unauthenticated user could view sensitive information for all users, and snoop on live class statistics and its attendees, despite having a private mode.
TL;DR
- Information disclosed included:
– User IDs
– Instructor IDs
– Group Membership
– Location
– Workout stats
– Gender and age
– If they are in the studio or not
- Unauthenticated endpoints were present which allowed users to interrogate information.
- Peloton says they have > 3 million subscribers, with over 1 million connected fitness subscribers.
- Famous figures such as the President of the United States use Peloton.
- Peloton acknowledged the disclosure, then ignored me and silently ‘fixed’ one of the issues. The ‘fix’ didn’t fix the vulnerability.
- 90 days later, we asked a trusted journalist to speak to Peloton on our behalf. This started a constructive conversation and resulted in the vulnerabilities being largely resolved.
Why Peloton?
Peloton make exercise bikes, top quality ones at that. The company is booming, in 2020 they announced a 113% increase year over year which they expect to double in 2021.
The real selling point is the app and subscription services that goes with them. It gives users access to live real-time classes and sessions with a coach, not just for the bike though. They also provide classes for their treadmill, yoga, and outdoor running.
A user can have access to all this for a very reasonable £12.99 a month.
There are so many good things to say about Peloton. Lockdowns and isolation are good for nobody so having an at-home exercise option, with human interaction is a blessing. It’s also great that they provide running and yoga classes, as they don’t require the investment in equipment, only a subscription.
What’s not to like?
The mobile, web application and back-end APIs had several endpoints that revealed users’ information to both authenticated and unauthenticated users. A full investigation should be conducted by Peloton to improve their security, especially now that famous individuals are openly using this service.
Issue 1: Class Information Snooping
This endpoint could have been polled by an unauthenticated user, but the ‘fix’ now requires a user account, which anyone can self-register to. This still exposes the same data to any other Peloton user.
Some of these classes can reach 800+ users at one time, which increases how much data someone could harvest.
Host: https://api.onepeloton.co.uk
Full URL/API Endpoint: https://api.onepeloton.co.uk/stats/workouts/details
API Request:
POST /stats/workouts/details HTTP/1.1
Host: api.onepeloton.co.uk
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: application/json, text/plain, */*
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 1794
Origin: https://members.onepeloton.co.uk
DNT: 1
Connection: close
Referer: https://members.onepeloton.co.uk/player/live/xxxREDACTEDxxx
Cookie: __cfduid=x; driftt_aid=x; DFTT_END_USER_PREV_BOOTSTRAPPED=true; peloton_session_id=x
{"ids":["x","x","x","x","x","x",]}
It should be noted that these “ids” are automatically populated when using the web application. These “ids” can be identified whilst using the mobile app and the request can be manually updated and sent.
It was possible for unauthenticated users to make this request, however, this has been resolved. Now only the 3 million authenticated Peloton users can see the data…
API Response
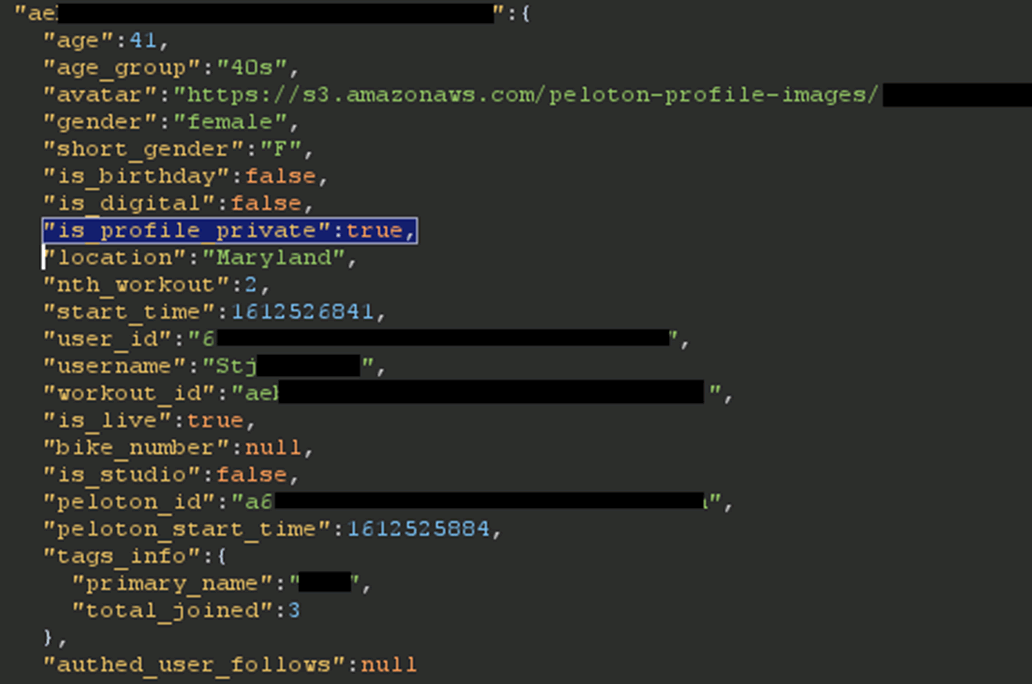
Personal data disclosed, despite profile being set as ‘private’
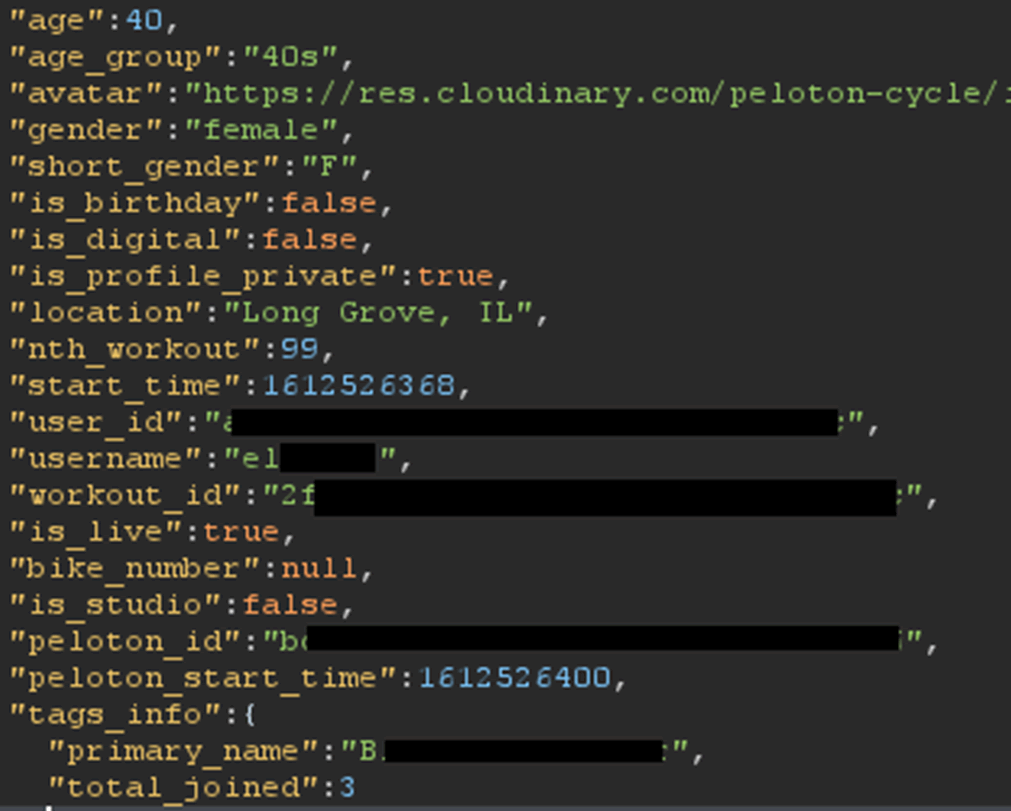
Another example of personal data disclosed, despite profile also being set as ‘private’
Issue 2: User Search Feature
Host: https://api.onepeloton.com
Full URL/API Endpoint: https://api.onepeloton.com/api/user/search/
API Request:
GET /api/user/search/test HTTP/1.1 Host: api.onepeloton.com Peloton-Feature-Include-Tread: true Peloton-Platform: iOS_app Accept-Encoding: gzip, deflate Accept: */* Connection: close Cookie: peloton_session_id=xxxREDACTEDxxx; path=/; domain=.pelotoncycle.com; Accept-Language: en-US Peloton-Client-Date: xxxREDACTEDxxxT11:25:16.016Z[Europe/London] User-Agent: Argon/14.9.0 (com.Peloton.PelotonApp; build:65887; iOS 14.3.0) Alamofire/5.2.2
API Response:
{
"id": "[USER_ID]",
"image_url": "https://peloton-profile-images.s3.amazonaws.com/[USER_PROFILE_PIC.png]",
"is_profile_private": false,
"location": "NYC",
"total_followers": [X],
"total_following": [X],
"total_workouts": [X],
"username": "[USER_NAME]",
"authed_user_follows": false,
"relationship": {
"me_to_user": "none",
"user_to_me": null
},
"category": "others"
},
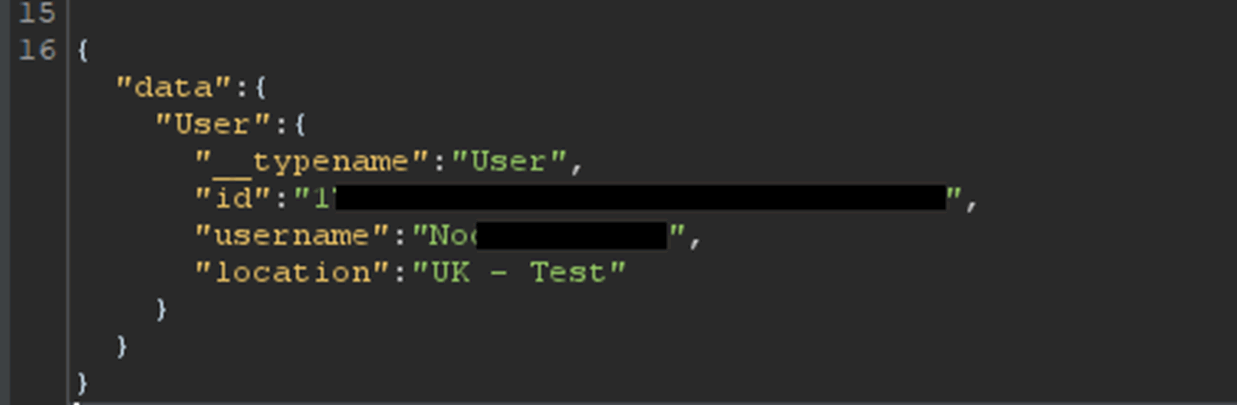
Issue 3: Unauthenticated GraphQL Endpoint
There were a number of GraphQL endpoints, some examples are gql-graphql-gateway.prod.k8s.onepeloton.com and gql-graphql-gateway.prod.k8s.onepeloton.co.uk, which allowed unauthenticated users to make GraphQL queries to access data.
API Request
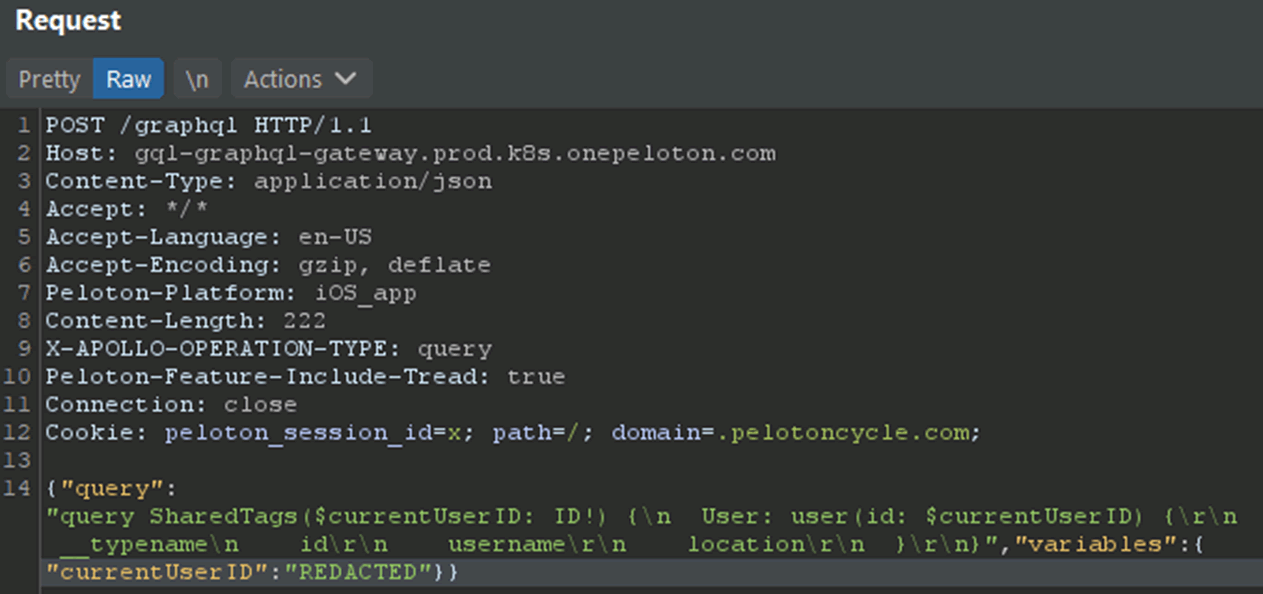
API Response (Sample)
Privacy Mode? Erm…
Many fitness apps have privacy settings that would limit the disclosure of personal information. We were initially concerned that the PII above was intentionally available, as the users had not applied privacy controls.
However, we set privacy on our own account and could still retrieve the data!
Peloton has two different privacy settings: private profile and hide my age and gender. Private profile restricts users from viewing your profile and hide your age and gender does that in online classes. Having a private profile does not protect all of your data when using Peloton’s classes.
Disclosure timeline
I was optimistic about this disclosure, as Peloton have a vulnerability disclosure programme, but I was wrong:
- 20th January 2021: disclosed privately to Peloton, as per their VDP.
- 20th January 2021: receipt acknowledged. This is the last we heard from Peloton.
- 22nd January 2021: we requested an update and offered assistance replicating the vulnerability. No response.
- 2nd February 2021: unauthenticated API endpoint issue was silently and partly resolved – user data was now only available to all authenticated Peloton users. Er…?
- 2nd February 2021: we asked for an update, given the silent fix. No response.
- After 90 days we asked a trusted journalist to speak to Peloton on our behalf.
UPDATE 5th May 2021
Shortly after contact was made with the press office at Peloton we had contact direct from Peloton’s CISO, who was new in post.
The vulnerabilities were largely fixed within 7 days.
It’s a shame that our disclosure wasn’t responded to in a timely manner and also a shame that we had to involve a journalist in order to get listened to.
In fairness to Peloton they took it on the chin, thanked us, and acknowledged their failures in the process. I wish all vendors were so honest and grateful.
Onwards and upwards.