TL;DR
- Data breaches make the headlines usually because of the sheer volume of data
- Research shows that often the volume of data is falsely inflated
- How forensics experts can spot it
Introduction
When a data breach hits the news, it’s usually all about the numbers: millions of names, emails, and maybe even credit card details stolen.
Sounds serious, right? But here’s the catch, sometimes *not all of that data is real*. Hackers will add fake stuff into these leaks on purpose, for example this is just a tiny snippet from what could be 2 million compromised accounts:
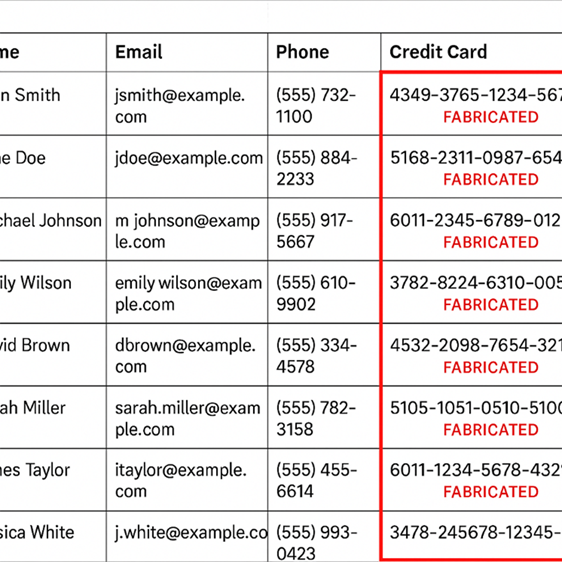
Yeah, really. As this is a small sample it’s easy to check by eye, not so easy if you’re dealing with huge amounts of data, more on that later.
Why would they do that?
At first it seems weird. Why would someone go through all the effort to break in somewhere, steal stuff, and then make up data on top of it?
Turns out, there’s a few reasons:
1. To make the leak look better
Leaks with credit card info sell better than ones with just names and emails. So if they only stole personal info, some hackers throw in fake credit card numbers to make the dataset look more valuable. It’s like dressing up garbage in gold wrapping paper.
2. To confuse the people investigating
Mixing fake stuff with real data makes it harder for cybersecurity experts to figure out where the breach came from. If the data looks like it’s from multiple sources, it throws people off the trail.
3. To cause more trouble
Sometimes, the goal isn’t even to sell the data—it’s to mess with the company that got hacked. Adding fake credit card info can make the company look worse than it really is, especially if they claimed no financial data was stolen.
How can you tell what’s fake?
It’s not always obvious, but here’s what to watch for:
- Weird formatting – credit card numbers that don’t start with the right digits or expiry dates that all look the same.
- Copy-paste data – same names or emails tied to lots of different cards.
- Missing details – real leaks often include recent transactions or bank names. Fake ones usually don’t.
- Patterns – like card numbers going up in order, or emails like bob1@gmail, bob2@gmail, etc.
How forensic experts can spot it
Cybersecurity folks use a few tricks to figure out what’s fake:
- BIN checks – they check if the card numbers are actually from real banks.
- Luhn algorithm – it’s a quick way to see if a card number is mathematically valid.
- Compare with old leaks – if the same info shows up across unrelated breaches, something’s fishy.
- Check for weird combos – like a UK address, US phone number, and a European bank card all in one record. It doesn’t add up.
Fake data in leaks isn’t rare, it’s a trick that hackers use more often than you’d think. It helps them make more money, throw off investigators, or just stir up chaos.
So next time you see a big headline about millions of credit card details being stolen, take it with a pinch of salt. There might be lies mixed in to bulk up the truth.















No Comments yet!