The aviation industry realised some time ago that taking a standard approach to the cyber security of its products was needed and that this was a specialist discipline.
A family of documents was produced to help with this:
- ED-202A / DO-326A – what should be certified
- ED-203A / DO-356A – how these should be certified
- ED-204A / DO-355 – once in service, now what
You’ll note there are two reference numbers: “ED-“ were produced by the European EUROCAE working groups and “DO-“ by the American RTCA special committees. The text is otherwise identical but depending on where an aircraft is certified the particular number is referenced. For the purposes of this post we’ll stick with the EUROCAE numbering but you can read it as both.
It’s important to say that cyber security airworthiness addresses only “intentional unauthorised electronical interaction” i.e. hacking. Physical attacks (taking a hammer to an LRU) are not relevant here.
What is the scope of testing for avionics?
During the scoping phase the avionics equipment, or indeed the whole aircraft, will need to be decomposed into its constituent assets and interfaces. This might include any USB interfaces, Ethernet ports, or debug access like JTAG. Data flows are also mapped, and security trust boundaries identified (e.g. systems that are accessible from the passenger cabin versus only the flight deck).
Only systems that are in the Major hazard class (threat conditions which would reduce safety margins or increase workload) or above are required to be covered by ED-203A but that doesn’t necessarily mean that lower hazard systems should not be evaluated.
Risk Assessment
Attack paths are created with scoring against each vulnerability and security control. These threat scores are derived from:
- Preparation means (public information versus insider knowledge)
- Window of opportunity (attack can happen any time through to specific flight modes only)
- Execution means (lay to expert, standard versus bespoke tooling)
The effective protection level is scored from 0 (none) to 30 (very high)
Every possible pivot through each node needs to be calculated with an overall residual risk assessed. This then shows whether the risk treatment and controls are below an acceptable level.
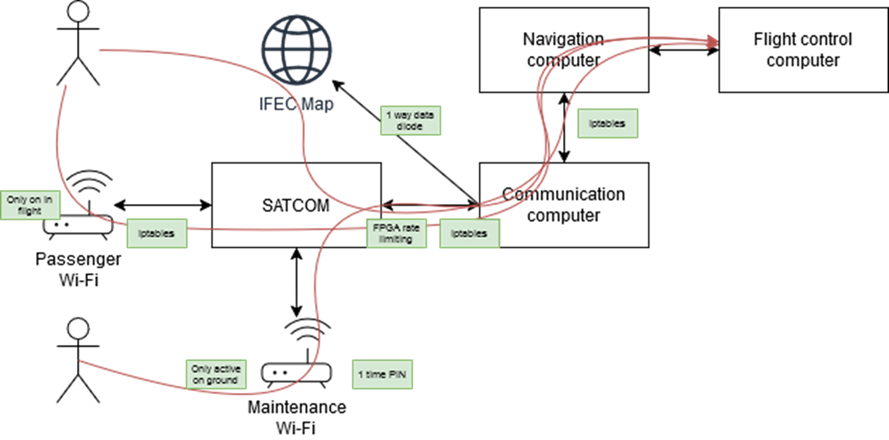
Note: this is just an illustration of a sample attack path and controls model.
Security Assurance Levels (SAL) are a classifier for the confidence in protection against attacks. These range from 0 to 3 with 3 being the strongest security assurance. These levels correspond with specific security objectives in ED-203A.
SAL should not be confused with Design Assurance Level (DAL) from DO-178C although the terminology is similar. DALs are for general safety consideration when desig















No Comments yet!