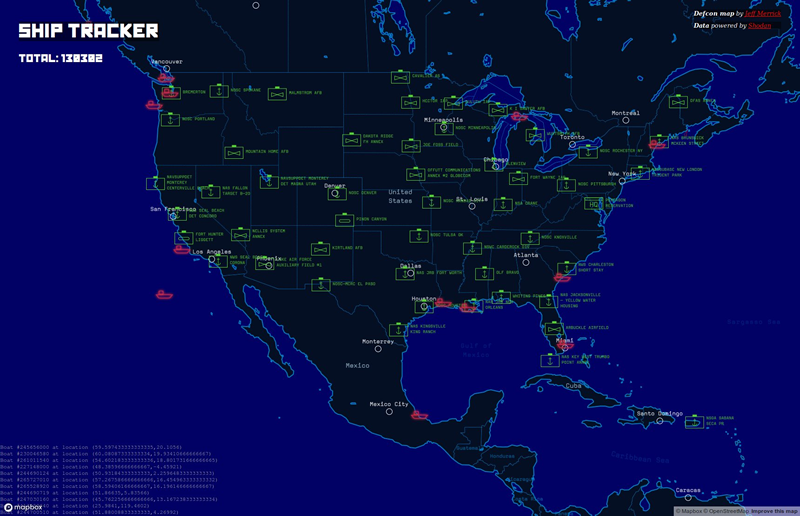
The graphical ship tracker released by @shodanhq is something of a game changer for maritime security, with a few tweaks.
The data one needs is already available, but requires a lot of manual work to analyse and present on a map. It is difficult to target a specific vessel, though this is how I carried out my previous research on data gathering from satcom units.
With additions, it could become trivially easy to select a potentially vulnerable ship on a map to attack.
How does it work?
As far as I can make out, the Shodan Ship Tracker is simply presenting AIS data, much as https://www.vesselfinder.com and https://www.marinetraffic.com and others do.
I hope I’m wrong and it’s doing more than that, but I’m not convinced that it is. The data displayed is GPS coordinates and vessel MMSI. That’s AIS!
What if you could mash up AIS and Shodan data together?
What if you could correlate AIS GPS coordinates with the satcom box profile on Shodan? Then you would have a real time map of ship by vulnerability…
Searching for terms such as:
- ‘inmarsat’
- ‘Sailor 900′
- ‘thrane’
- Etc.
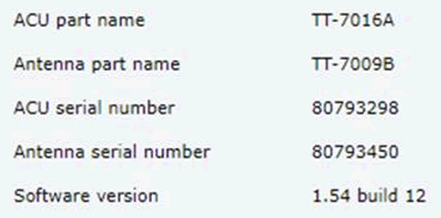
…can give you the web interface of some satcom boxes. One can often find out the firmware version running on the satcom unit itself.
Here’s a Cobham satcom box running at firmware version 1.54 – that’s way out of date – I believe the current version is 1.60 build 015
Linking up AIS and Shodan
Shodan doesn’t often pick up the actual location of the satcom box: Here’s the above ships satcom receiver – it reports its position as being on the north side of Oslo. So how do we make this data more useful?

If we add in AIS data to our ship tracking efforts, we get everything we need to ID and locate the ship.
Here’s the web interface of the above Cobham Sailor 900 VSAT Ku satcom box. Even without authenticating we can see GNSS position and heading data:
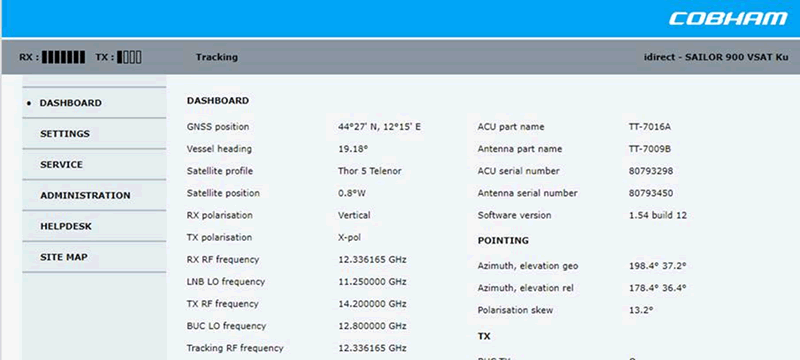
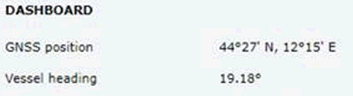
If we use the GNSS position from the box itself, we can see the ship was actually in the port of Ravenna when I wrote this, near Bologna. Not Oslo:
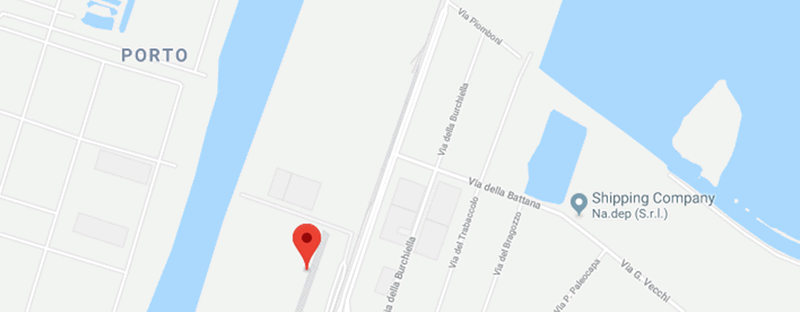
Now, if we compare with AIS data, we can see the vessel is almost undoubtedly the MSC Lea:
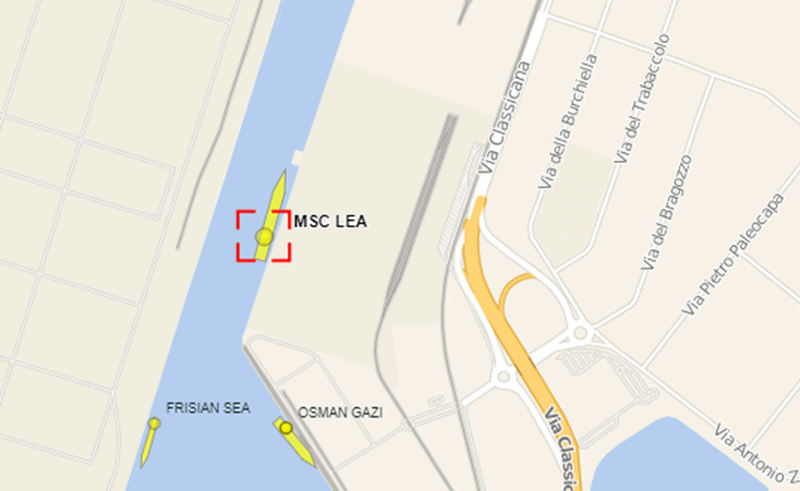
We can see that it’s facing on a heading of roughly 020, making it the only ship in the port that matches the heading data from the satcom unit.
Here’s what it looks like; a container ship that would be an interesting target for many of the attacks I’ve described here.

So my next task is to attempt to automate the manual process of matching GPS coordinates from the satcom box with the current GPS coordinates displayed on AIS.
Then you have a graphical map of ship location by vulnerability in the satcom box. That’s a killer.
Recommendations
Securing your satcom box is critical. Get the latest updates from your satcom provider and apply them urgently.
Make sure your satcom admin passwords are changed from the default and are not simple words.
Many satcom providers have moved to private connections, so that the box isn’t visible on the public internet. This is a wise move.